A No-attack Mode Is Used Best Under Which Circumstance
To help you determine if this is a problem for you we have also listed some diagnostic questions to serve as warning signals for the under or overuse of each mode. The connection utilizes the 80211n standard.
The force used in defence must be not only necessary for the purpose of avoiding the attack but also reasonable ie.
. To solve this probability we apply the binomial formula twice. The connection is followed by a VPN connection to a trusted network. In a spoofing attack the attacker doesnt actively take over another user to perform the attack.
Proportionate to the harm threatened. A phishing b spoofing c hijacking d vishing Answer. 000 043.
Available in TK Dodge SE or TK Dodge RE - Script Free. Using lower-cost ATGMs to attack slow-flying helicopters under certain circumstances allows for less plentiful and more advanced missiles to be saved for other targets that might demand their. A mode of attack is a method by which hackers seek to access a system.
To find the mode sort your data set numerically or categorically and select the response that occurs most frequently. Email attachments Buffer overflow Security software Updating processes and. Finding the mode In a survey you ask 9 participants whether they identify as conservative.
It also doesnt need padding data. The device has been updated with the latest virus protection software. The mode is the most frequently occurring value in the data set.
Feel free to comment or edit the answer to improve it. If you use another evasion related mod with a higher number than that number it wont work. The DAR condition folder number is 70120.
4 also enables a block encryptor to be used as a stream encryptor. This can be reduced several times and under the best circumstances an attacker needs 2¹³ TLS sessions to recover one plaintext byte. The most commonly used session hijacking attack is IP spoofing.
The OFB Output FeedBack mode of operation Fig. No one wrote a complete answer so I will try to incorporate the comments and partial answers into an answer. Specifically we want Pno more than 1 success P0 or 1 successes P0 successes P1 success.
Normally normal dodge is used but if you dodge during an attack it will attack at the same time as dodging. To ensure security the key in this mode need to be changed for every 2n12 encryption blocks. Timing Attack results in long red and short blue fake padding AlFardan Paterson 2013.
In other words 0 or 1 but not more than 1. Under certain circumstances a fire attack may be too dangerous and incident command will choose to let the fire burn out without an attack Cannot be made without careful consideration and by making every effort to include the owner in the decision making process. For the purposes of this question and answer userspace to kernel transitions mean a change in processor state that allows access to kernel code and memory.
To utilize each mode in the appropriate situation. There is a possibility that your social skills lead you to rely upon some conflict behaviors more or less than necessary. Its possible to have no mode one mode or more than one mode.
In its most basic version a LUCKY 13 attack requires about 223 TLS sessions to collect a whole block of TLS-encrypted plaintext. Under which circumstance is it safe to connect to an open wireless network. Modes of attack include.
In this mode it will encrypt the IV in the first time and encrypt the per-result. Hackers exploit system vulnerabilities in order to damage data or interrupt computer functions through code manipulation or by injecting new malicious code. Suppose in the heart attack example we wanted to compute the probability that no more than 1 person dies of the heart attack.
The rule is best stated in the negative form that the force must not be such that a reasonable man would have regarded it as being out of all proportion to the danger. In _____ attack the attacker doesnt actively take over another user to perform the attack. Attack Modes contd Non-attack mode passive approach.
What Is Fishbone Diagram In Six Sigma Quora
Is Aspergers The Highest Functioning Form Of Autism Quora
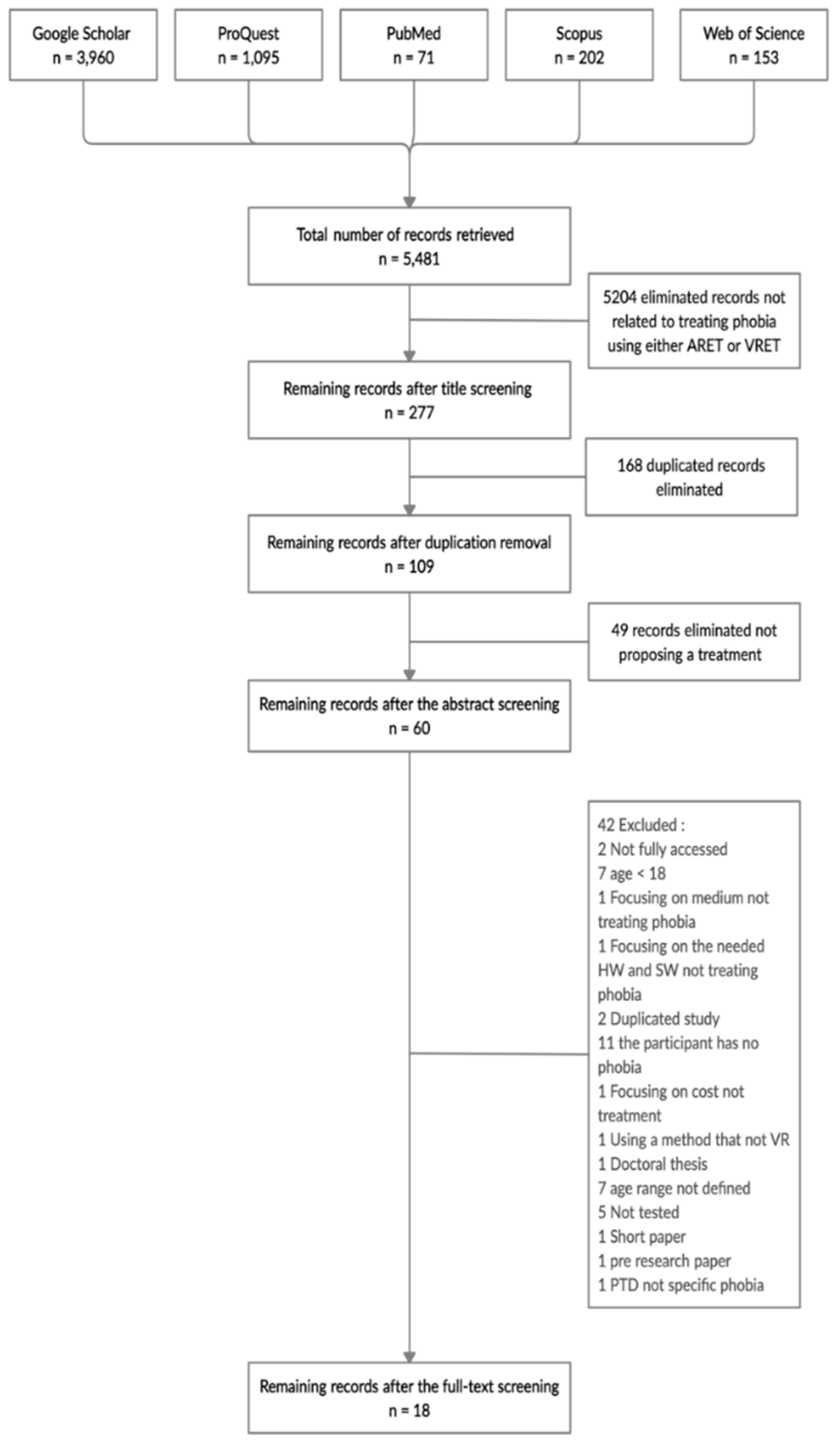
Applied Sciences Free Full Text Phobia Exposure Therapy Using Virtual And Augmented Reality A Systematic Review Html

Japan Has A Shortage Of Ninjas And New Recruits Lack The Skills Needed To Be One Geektyrant Martial Arts Ninja Art Ninja
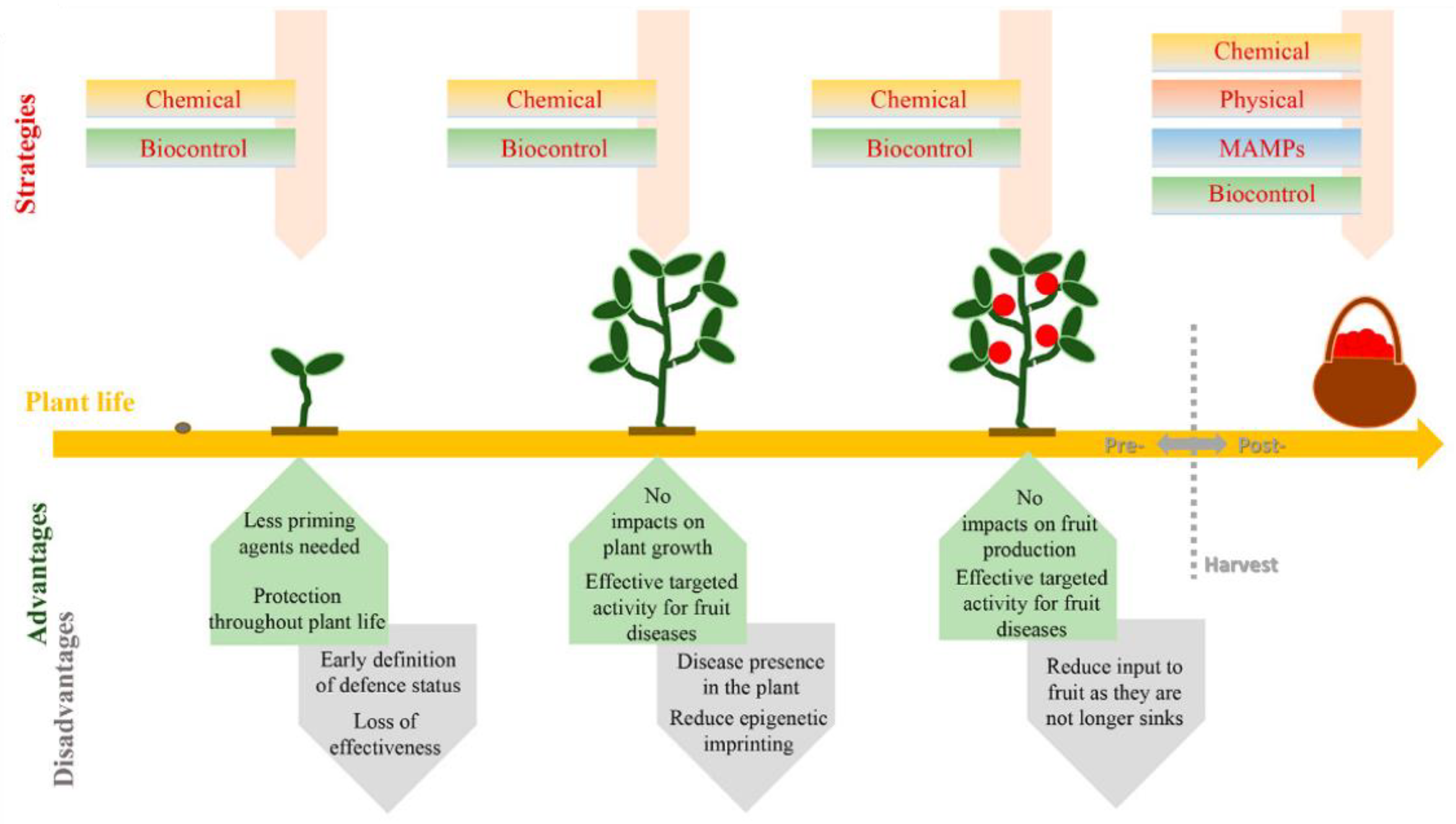
Fermentation Free Full Text Microbial Biocontrol As An Alternative To Synthetic Fungicides Boundaries Between Pre And Postharvest Applications On Vegetables And Fruits Html

Take Out Your Reference Packet And Paper To Take Notes Ppt Download

Pdf The Role Of Context In The Interpretation Of Pragmatic Meaning

Hydraulics Ppt Video Online Download

Pdf Does Work For The Dole Work An Australian Perspective On Work Experience Programmes
Pdf The Vulnerable World Hypothesis

Multilingualism In Democratic South Africa The Over Estimation Of Language Policy

Pdf System Quality Requirements Engineering Square Methodology Case Study On Asset Management System
Comments
Post a Comment